SOLUTIONS ONLY
a place of learning there cant be a problem without a solution
Wednesday, April 20, 2011
Africa in search of true and good leadership
Not that the Mo Ibrahim Prize committee didn’t short-list anybody, it was said that the prize committee has considered some credible candidates. However, after an in-depth review, the prize committee could not select a winner. Former presidents Thabo Mbeki (South Africa) and John Kufor (Ghana) were among the short-listed candidates for the prize.
Launched in October 2006, the Mo Ibrahim Prize is awarded to elected African presidents and prime ministers who have left office within the last three years to encourage African leaders to leave office with good name and works the same way that Nelson Mandela did in South Africa. He served only one term in 1994. These criteria automatically prelude many African leaders from eligibility.
As the committee acknowledged that governance improved in some other African countries while some country’s governance were nothing to write home about.
The past winners of the leadership prize; Festus Gontenbanyes (former president of Botswana) in 2008, Joaquin Alberto Chissano (president of Mozambique) in 2007 and Nelson Rulihlahla Mandela for his extraordinary leadership qualities and achievements.
A principal counsel and solicitor (name withheld) said “the news does not come as a surprise, albeit a sad reflection of the fact that Africa is facing a critical challenge of leadership and statesmanship in political sphere”. He also expressed regrets over Nigeria and South Africa, two countries in the African continent which, in spite of the different routes to statehood they separately tread, have the potentials to help push Africa to be a par with the rest of the industrialised continents of the world.
A legal practitioner (name withheld) also said “good leadership cannot be exercise in charismatic relationship while not being visionary or meeting people’s needs and gaps in basic to strategic interest and rights”. You cannot have a bad human right record and be exempting in economic growth. This is the third year of the award, but it is empirical evidence that we truly have no leadership in the continent.
Notwithstanding, a lawyer (name withheld) said that “good leadership has been a vanishing commodity for sometimes in Africa and that only a revolution world produce a new set of true leaders”.
It is rather unfortunate that Africans lack a good but unimaginable leadership. The struggle for independence has thrown up some of the finest leaders would have seen. The revolutionized leaders now are still small but are now been polluted with corruption camouflaged as ‘Normal Youth Life’
A TYPICAL NIGERIAN POLITICAL ADVERT
We require appointment as a people representative at a law making house, a proven hooligan with the following professional qualifications;
First degree in boxing or kicking boxing
A diploma in aggressive cover-up techniques
Must bee a dully certified liar with vast experience in corrupt practices
Must be ready to shun the voice of people in allegiance to the party’s wishes
Possession of a falsified educational degree will be a an added advantage
He must also have that additional advantage of speaking ands painting the picture of hell that every one will be willing and ready to go there without been forced
Thursday, January 20, 2011
Differences Between SP2 & SP3


# Microsoft's Windows XP operating system contains three service packs released over the past several years. While the first service pack provided minor updates to the operating system, the second and third releases provided updates for users who do not want to switch to a new Windows system. Service Pack 3, released in 2008, updates 2004's Service Pack 2.
Overview of Windows XP
# Microsoft released the Windows XP operating system in October 2001. Windows XP provided upgrades from its Windows 2000 and Windows Millennium Edition software. These upgrades included faster start-up times, increased support for hardware drivers and remote desktop functionality, which allowed users to access their computer from other locations. Despite Windows releasing two subsequent operating systems, Windows XP is still the most widely used operating system in the world.
Service Pack 2
# Windows released its second service pack for Windows XP in 2004. In addition to including all previously released updates, Service Pack 2 included new features including Windows Firewall, Security Center and Windows Media Player 9. Microsoft also included security updates for Outlook Express and Windows Messenger, its e-mail and instant-messaging programs. Many of the security features are used in subsequent Windows releases.
Service Pack 3
# Microsoft released its third and final service pack for Windows XP in 2008. Microsoft originally planned to release Service Pack 3 several years before, but the development and release was delayed due to Microsoft preparing its new Windows Vista system. Service Pack 3 is the final major update for the Windows XP operating system. However, Microsoft recently announced that it will continue to offer support and security updates for XP systems running Service Pack 3 until 2014.
Enhanced features
# In addition to adding new features, Microsoft's Service Pack 3 included updates to features from Service Pack 2. One such update is Windows Installer 3.1. This update corrects several issues from Windows Installer 3.0, such as fixing the progress bar during installation and allowing patching of isolated files. Service Pack 3 also included Remote Desktop 6.1, which allows people with XP computers the ability to connect to computers running Windows Vista. It also includes support for the Wi-Fi Access 2 security standard, a standard previously unsupported by XP.
New Features
# Service Pack 3 also included several new features. One such feature is an improved security control panel. The new panel includes more-descriptive text to explain settings. This helps keep users from selecting incorrect security settings for their computers. Another new feature is no-key installation. This allows users to install XP with Service Pack 3 without needing a registration key. Service Pack 3 also now turns on black hole router detection by default. Black hole routers silently discard information packets, leading to information being lost in transmission.
The Difference Between Windows XP and Vista


It would seem that most individuals have become so accustomed and comfortable with using Windows XP that many don’t want to make the transition over to the Windows Vista. Technically, we are creatures of habit so when it comes to making changes it’s not all that easy.
Like most things there are good and bad points about both XP and Vista.
The start menu is more advanced in Vista compared to XP. With Vista, you have a much broader range of search leverage. Another significant change is in the “All Programs” area. XP can be somewhat of a problem to keep the programs organized when you have several whereas with the Vista the programs are scrolled within the start menu making it much less confusing when you want to find a particular program.
Everyone finds the “All Programs List” in XP frustrating. It can be overwhelming with its 3 column wide display. Now in Vista the folders open and close with a single click. In addition to this in Vista, the ability to search is always present. This way to find something you just type the item and all related items appear quickly.
In Vista there is a power button in the bottom right hand corner. This allows all the pending updates to be installed and then once the update process is completed puts the computer into sleep mode. This is not something that XP has.
In XP when you want to perform the lock function you have to press Ctrl-Alt-Del whereas in Vista there is a simple lock button that will perform the task. In addition to these power functions, you will find other related power functions available to you by way of a pop up menu. In essence, these are all merely time savers and a means of convenience.
According to Microsoft, security of Windows Vista is much improved than XP. As part of this, a new feature called UAC (User Account Control) is included in Vista.
One of the critical differences between both, is the hardware requirements. To achieve the same level of performance as XP, Vista requires more advanced or additional hardware .
Quite often, when one becomes comfortable with a Program such as XP, they really don’t place a lot of emphasis on small time savers .
Saturday, January 8, 2011
Troubleshooting SSL related issues with IIS
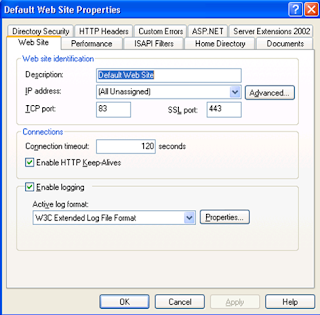
| In this post I am going to discuss troubleshooting SSL server certificate related issues in IIS. Please remember I am no SSL expert...I am an IIS Asp.Net guy and will discuss issues with regard to SSL with IIS. We have seen a lot many times that the issues could have been resolved by our customers if they were aware of some targeted troubleshooting techniques. Here I will be walking through the steps which you can follow yourself before requiring to call Microsoft PSS. Problem Description The most common error associated with SSL not working for an IIS website is "The page cannot be displayed" or "Cannot find server or DNS Error". Troubleshooting steps to be followed: My topic today is SSL with IIS so I won't be focusing on HTTP. We have the SSL port listed in IIS mmc as shown below. By default it's 443. You can configure it to listen on a different port.
Now, also check whether the issue is happening for all the users, i.e. External and internal users to the network. If the issue is happening only for let's say external users check whether the requests are coming over a firewall like ISA etc. At times Firewalls may block the SSL port. You may want to check the firewall settings to unblock the SSL port. Also firewalls like ISA requires certificate to be published on it as well apart from IIS server. Ensure that the certificate that we have installed on ISA is valid. In case of ISA, if you have renewed the cert on IIS server but not on ISA users will still see the old certificate and not the new certificate. Ensure that you replace the old certificate on ISA with the new certificate. Also you may want to check if the security gateway (if any) such as NFUSE (Citrix) controllers is still referencing the old certificate. Also at times if you see a wrong certificate being displayed for your Web Site, ensure that you do not have kernel-mode SSL enabled on your web server.Although this improves the performance but I recommend to have it disabled when you have multiple SSL enabled-websites on your server. Kernel-mode SSL is only recommended if you have just one site, mostly static content and no client certificates. In all other cases you should use User-mode SSL. Please find this link to enable/disable kernel-mode SSL. If it is set to 1 it means Kernel-mode SSL is enabled, if absent or set to 0 it means disabled and user-mode SSL will be used. Ensure that you stop and restart http service as shown below after doing the changes. No reboot is required for the above change. >net stop http >net start http >net start w3svc [There has been few concerns from people as to why this is suggested. I do not have a proper answer to it at this point, but I have seen such issues in some support incidents where disabling Kernel mode SSL had resolved the above problem] ------------------------------------------------------------------------------------------------------------------------------------------------------------------ Now once you have isolated the issue to be only with HTTPS and all users let's proceed with the following steps: Run netstat -an (or fport.exe) for IIS 5 (and netstat -ano for IIS 6) and verify whether IIS is listening on the SSL port. When you start Internet Information Services (IIS) 6.0 on Microsoft Windows Server 2003, IIS binds to all IP addresses on the server, not just the IP addresses that are assigned to Web sites. This is because of socket pooling enabled for IIS by default. On IIS 6.0, if the website is listening on "All unassigned" IP address or some specific IP address (like 192.134.123.209 etc) and SSL port 443, verify that Local address entry is 0.0.0.0:443 in netstat output. > netstat -ano Active Connections Proto Local Address Foreign Address State PID TCP 0.0.0.0:443 0.0.0.0:0 LISTENING 4 Here the PID should show you which process is listening on that port. Also you won't see the netstat output showing anything like this depending upon the port being used: TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:443 0.0.0.0:0 LISTENING 4 You can run netstat -ano again and see the PID corresponding to the process which is listening on that port. Stopping or disabling that service/process should allow Websites to be up and listening on the desired port. For IIS 5.x you can run Fport.exe to find out which process is listening on a specific port. The first thing that I check for (strictly my personal preference) when we have issues with SSL is MACHINEKEYS. Yes, this is a very important (I prefer to call strategic) part of your checklist while dealing with SSL issues. In my personal experience it has resolved a lot of issues for our customers. By default machinekeys folder should have permission for Administrator, System and Everyone according to this KB278381. Ensure that we inherit the above permission for all child objects under the machinekeys folder, that way all the machine keys have the necessary permissions. This is done by clicking the "Advanced" button on the security settings page, Clicking the check box "Replace permissions entries on all child objects...." and Another reason for the above error ('The page cannot be displayed') can be if you do not have a private key corresponding to the SSL server certificate. You can check that by opening the IIS mmc -> <<YourWebSite>> ->Properties ->Directory Security ->Secure Communications ->View certificate ->General -> "You have a private key that corresponds to this certificate" as shown below. If you do not see the above then SSL won't work for your website. To associate the certificate with its private key, we run the following command: > certutil -repairstore my "c9 66 67 68 49 97 88 7f 05 b8 89 b7 b3 f7 37 c8 c4 da 5f 16" Note: "c9 66 67 68 49 97 88 7f 05 b8 89 b7 b3 f7 37 c8 c4 da 5f 16" is the Thumbprint of the missing certificate. You can see this if you double-click on the .cer file, choose the Details tab and select Thumbprint. Make sure you use the 2003 version of certutil.exe (with the associated certadm.dll and certcli.dll), or you will not have access to the repairstore command. If the above command does not get back the private key or for some reason it still does not work you may prefer to get a new certificate from the CA. One of the best tools that Microsoft has come up with is SSL Diagnostics to troubleshoot SSL related issues. Just download it to the IIS server and run it and if there is an error due to configuration of IIS or certificate it will show up. You can also use this tool to issue a test certificate for your website to check whether the problem was occurring because of your server certificate or some other IIS configuration related issues. Things that can be shown quickly through this tool includes on "no private key", "SSL port being used by a different process", "machine keys not having enough permission", "IP address conflicts" etc. Another scenario can be wherein if you view the certificate, it will state that "You have a private key that corresponds to this certificate," and if you run SSL Diagnostics, you'll get the error as below: #WARNING: You have a private key that corresponds to this certificate but CryptAcquireCertificatePrivateKey failed When you initially go through the IIS Certificate Wizard to create a new certificate, a file is added to the MachineKeys folder. This is the private key. If you add permissions to the new file in the MachineKeys folder before you process the pending request in the IIS certificate wizard, the certificate |